Explain the Different Types of Attacks on Digital Signatures
This attack is similar CPA. Remote digital signature.

Digital Signatures What Are They And How Do They Work
A digital signature is a type of electronic signature that offers more security than a traditional electronic signature.
. But there are many different types of electronic signatures each allowing users to sign documents digitally and offering some degree of identity authentication. Taking Advantage of Vulnerabilities. Question 4 Explain different Kinds of Malicious Code.
Either by constructing a new message for an existing digital signature. At face value digital signatures can look a lot like digitized signatures. Question 3 Write a note on Digital Signature.
Instead it is launched to exploit the weakness in physical implementation of the cryptosystem. The difference happens behind the scenes. Use Digital Signatures - Digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document.
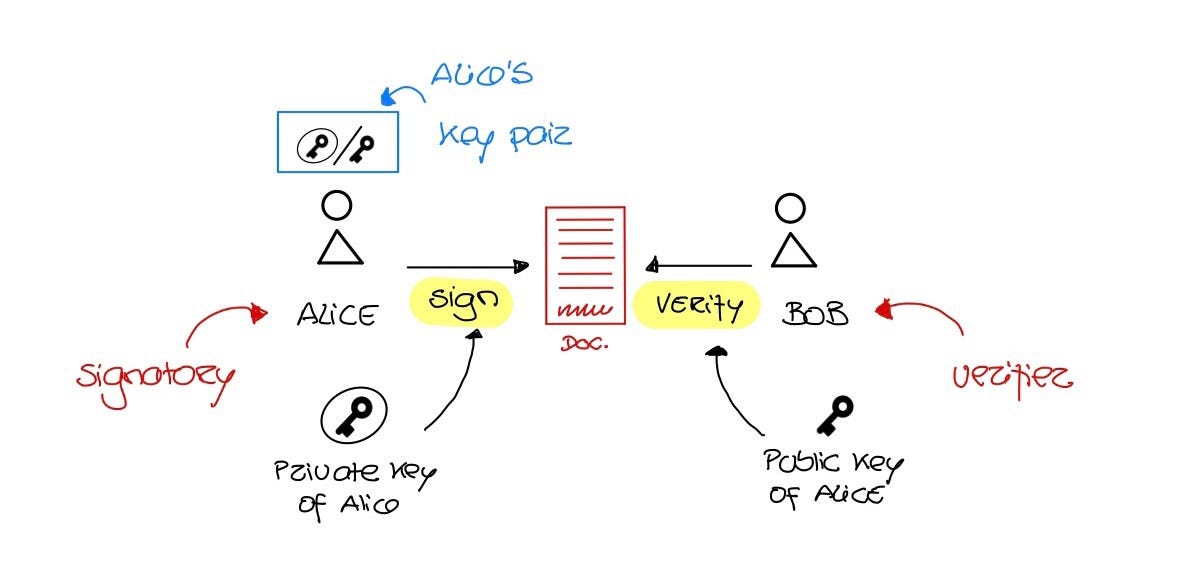
The instant you sign a document with a digital signature the document is. This signature appears on a document in the same way as signatures are signed on a physical document. Public and private keys can be used.
Side Channel Attack SCA This type of attack is not against any particular type of cryptosystem or algorithm. The visible digital signature allows a user to sign a single document digitally. This appendix includes 117 attacks on digital signatures that have been classified using the taxonomy and method of classification proposed in the paper.
3 types of digital signature are being used mentioned below. Its the hardest to implement but is the most probable attack as only ciphertext is required. It is a safe and agile mechanism Validate ID explains.
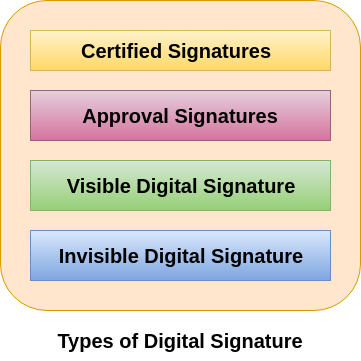
Classes and types of digital signatures. Similarly a digital signature is a technique that binds a personentity to the digital data. There are three different classes of digital signature certificates DSCs.
It is also known as G S and V. The surveyed attacks are a mix of real-world attacks on specific commercial products and devised theoretical attacks that could be put into practice. 14 Attacks - Types of Attacks Expandcollapse global location 14 Attacks - Types of Attacks.
When you sign a document with a digital signature the signature. Digital signatures are the public-key primitives of message authentication. Question 2 What are the Characteristics of Good Encryption Technique.
This document also provides an explanation of the differences between direct and arbitrated digital signatures. They can be drawn using a finger on an iPad or created with the click of a mouse. DS makes it possible to ascertain the non-distortion status of information in a.
Now C tries to. There can be other attacks like key only attack know message attack and adaptive chosen message attack. In this type of attack attacker intercepts the messagekey between two communicating parties through a secured channel.
Abstract The purpose of this document is to explain specific properties that a digital signature should have. To each of these types security. A digital signature is a means by which the sender can electronically sign the data and the receiver can electronically verify the signature.
Here A denotes the user whose signature method is being attacked and C denotes the attacker. Timing Attacks They exploit the fact that different computations take different times to compute on processor. In the known message attack C has few previous messages and signatures of A.
The methods extend from a simple theft through network infiltration to extensive research attacks stuffing different key combinations to guess the correct one. Class 1 signatures provide a basic level of security and are used in environments with a low risk of data compromise. Question 5 Write a short note on Encryption.
Adaptive Chosen-Plaintext Analysis ACPA. It is a signature that is done online on a PDF or Word document without the need to install any kind of program. Question 6 Explain on Secure E-Mail System E-Mail.
GOLD88 lists the following types of attacks in order of increasing severity. How Can Simplilearn Help You. Learn the types of attacks on a system the techniques used and more with the Certified Ethical Hacking Course.
Which could look for different signatures which represent an attack. Man-In-The-Middle MITM attack. The chosen attack method is of two types.
There are different types of forgery. In a cryptographic digital signature or MAC system digital signature forgery is the ability to create a pair consisting of a message m displaystyle m and a signature σ displaystyle sigma that is valid for m displaystyle m but has not been created in the past by the legitimate signer. True digital signatures are a type of electronic signature but they arent the same thing.
C only knows As public key. Different Types of Digital Signature. Question 1 Explain the types of threats Attacks.
A less conventional method to overturn digital signatures is exploiting the vulnerabilities that occur during their execution. In the physical world it is common to use handwritten signatures on handwritten or typed messages. Just because theyre easy to use doesnt mean they are the same.
In this two entities exchange some messages to prove their identity to each other. Using Encryption mechanisms. Cannot be used for legal business documents as they are validated based only on an email ID and username.
Digital signatures are one of those electronic signature technologies and are the most secure type available. A digital signature is the detail of an electronic document that is used to identify the person that transmits data. Or by constructing a fraudulent digital signature for a given message Practical to retain a copy of the digital signature in storage.
Generic chosen-method In this method C tricks A. Two general schemes for digital signatures. The invisible digital signatures carry a visual indication of a blue ribbon within a document in the taskbar.
They are used to bind signatory to the message. Heres our quick guide to the difference. By measuring such timings it is be possible to know about a.
Classified attacks on digital signatures. To guarantee security a double validation is always carried out via email and OTP One Time Password to the signers smartphone with which they. Hope this article has helped you understand how vital digital signatures are in this digital age and the impact of cryptography in shaping the threat model of our corporate sector.
It helps save the message and document from several attacks. Lastly this document explains what a suppress-replay attack entails.
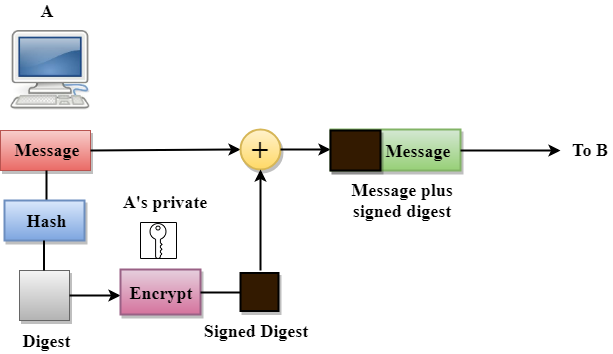
Computer Network Digital Signature Javatpoint
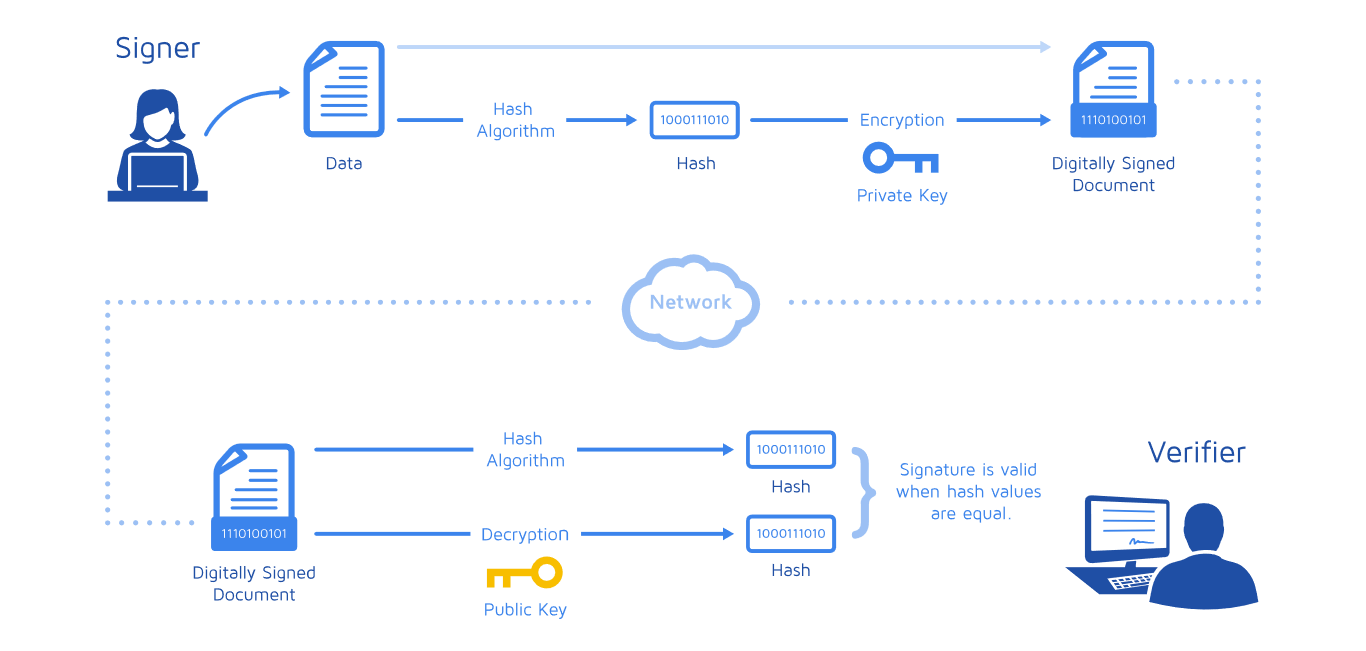
Digital Signature Generation Digital Signatures Are Like Electronic By Meruja Selvamanikkam Medium

Remote Digital Signatures And Eidas Regulation By Barbara Vieira Medium

Digital Signature Types Recognize 3 Major Class Of Digital Signature
Cybersecurity Digital Signature Javatpoint

Pdf Digital Signature Scheme For Information Non Repudiation In Blockchain A State Of The Art Review

Digital Signature Algorithm How It Works Advantages Disadvantages
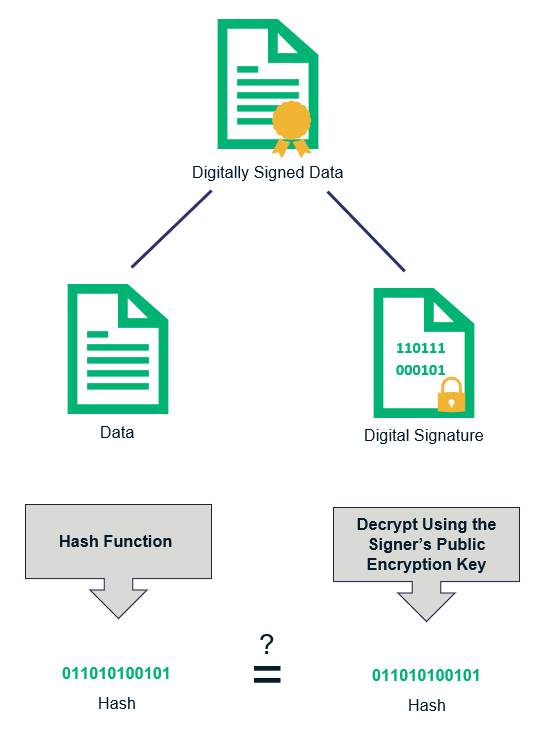
What Is A Digital Signature And How Does The Digital Signature Process Work Infosec Insights

What Is A Digital Signature Fundamental Principles Security Affairssecurity Affairs
What Is A Digital Signature Types Of Attacks On Digital Signature
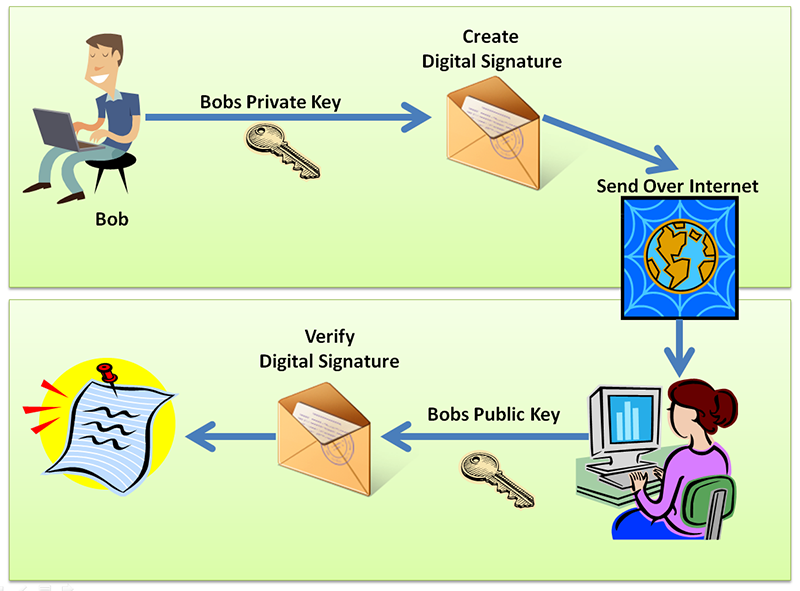
Digital Signature Example And Digital Signature Processing
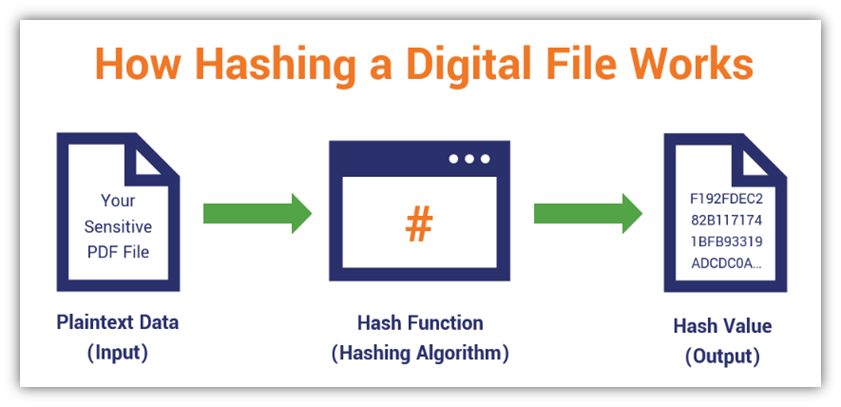
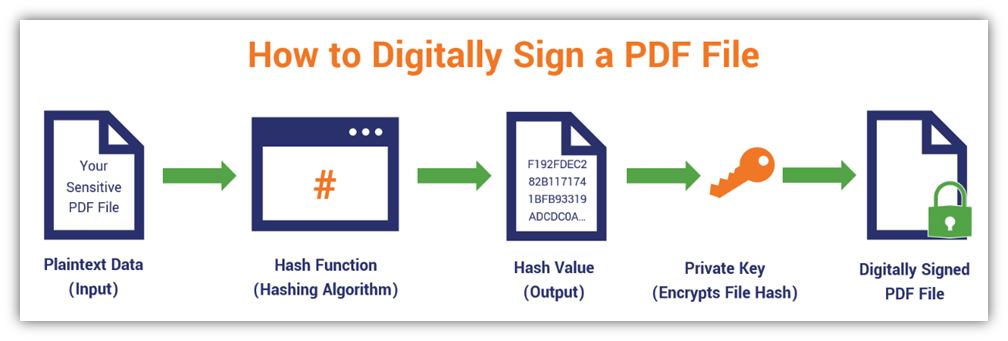
How Do Digital Signatures Work A Look At How A Pki Signature Works Hashed Out By The Ssl Store
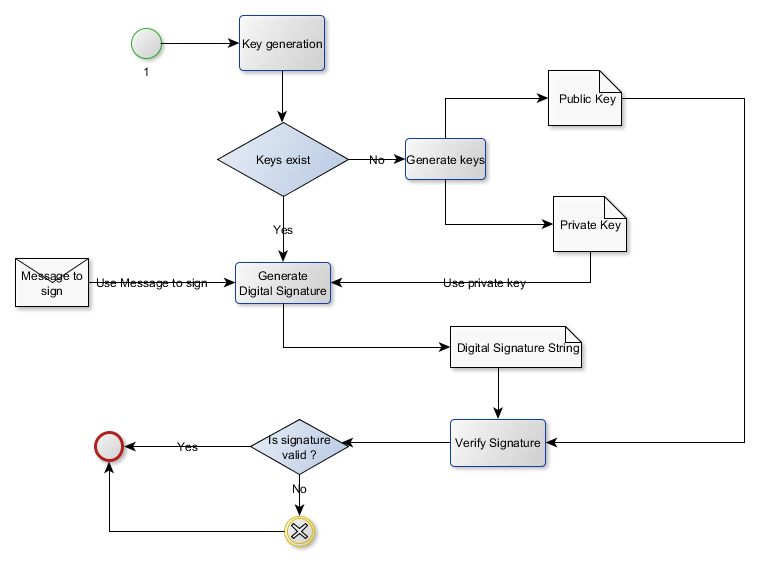
Digital Signature Generation Digital Signatures Are Like Electronic By Meruja Selvamanikkam Medium
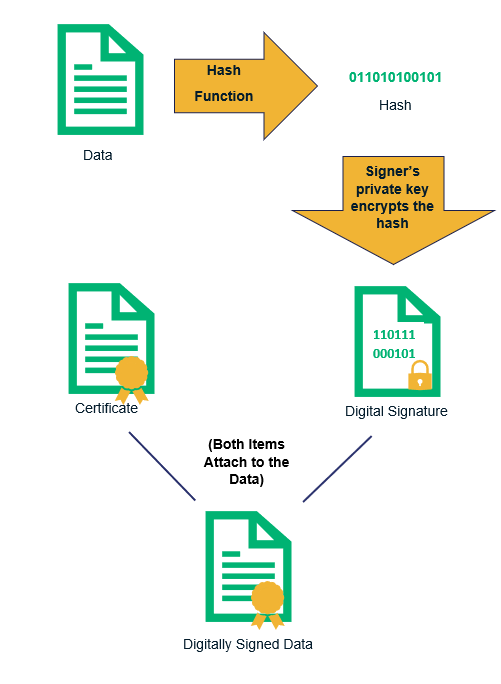
What Is A Digital Signature And How Does The Digital Signature Process Work Infosec Insights
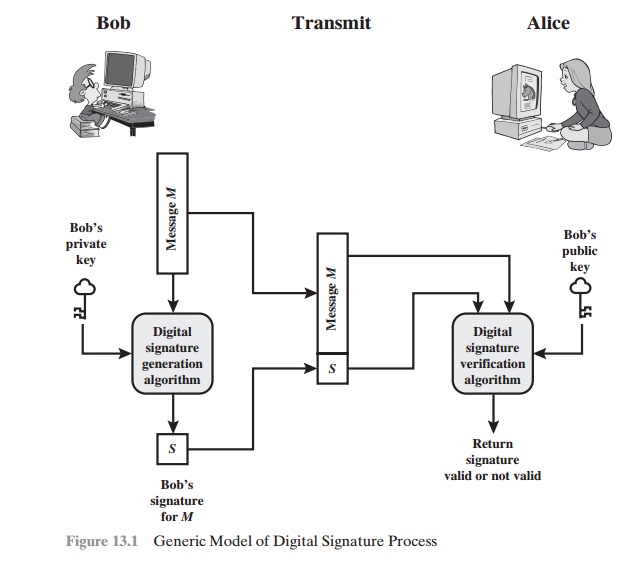
Digital Signatures Properties Attacks And Forgeries

Digital Signature Cryptography Know 2 Major Forms Of Encryption
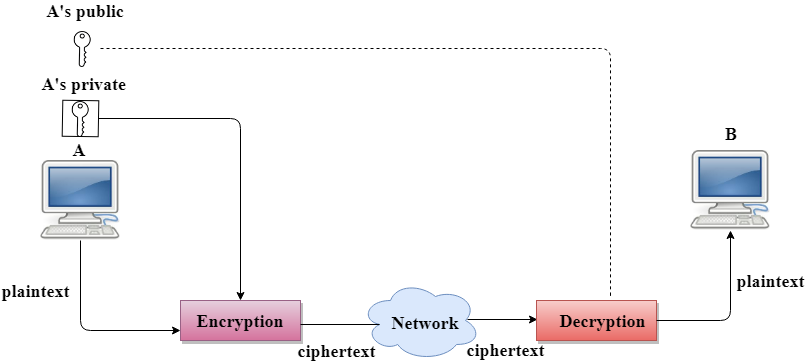
Computer Network Digital Signature Javatpoint
How Do Digital Signatures Work A Look At How A Pki Signature Works Hashed Out By The Ssl Store

Comments
Post a Comment